Table of Contents
Understanding Identity Governance Fundamentals
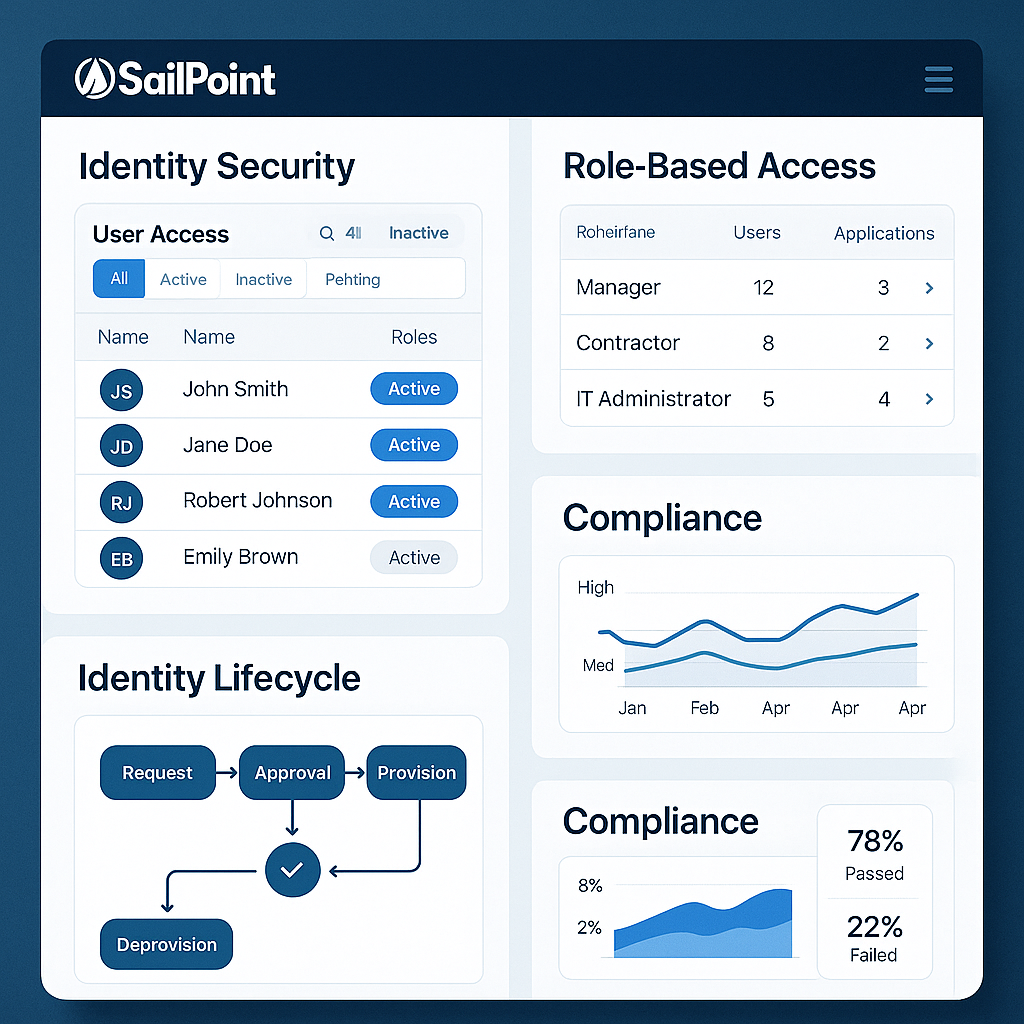
In any enterprise security discussion, the conversation often gravitates toward firewalls, intrusion detection, and endpoint protection. These are vital, but they primarily answer the question, “How do we keep threats out?” A more fundamental and often more complex question is, “Who has access to what, and should they?” This is the domain of Identity Governance and Administration (IGA), a critical discipline where SailPoint has become a dominant force.
Field-tested perspectives from decades of systems work highlight a pervasive problem: access creep. Employees change roles, take on temporary projects, or simply accumulate permissions over time. Without a robust governance process, this creates a massive, often invisible, security risk. An IGA platform like SailPoint is designed to bring order to this chaos, ensuring that access privileges are always aligned with business needs and security policies.
Beyond Basic Access Management
Core IGA Challenges and Solutions
It’s important to distinguish IGA from other identity management concepts. While a Privileged Access Management (PAM) solution like CyberArk focuses on securing high-level admin accounts, IGA provides the overarching framework for all identities (human and machine). It addresses three core challenges that are nightmares to manage manually:
- Access Certification: For compliance with regulations like SOX, HIPAA, or GDPR, companies must regularly prove that only authorized individuals have access to sensitive financial systems, customer data, or intellectual property. SailPoint automates these access review campaigns. It presents managers with a clear dashboard of their team’s permissions and prompts them to certify or revoke access, creating a crucial audit trail. This significantly reduces the burden of manual reviews and improves compliance posture.
- Lifecycle Management (Joiner-Mover-Leaver): The JML process is a classic operational headache. IGA platforms automate it. When a new employee joins (Joiner), the system can provision baseline access based on their role, ensuring they have what they need from day one. When they move departments (Mover), it can revoke old permissions and grant new ones, preventing unnecessary access accumulation. When they leave (Leaver), it ensures all access is terminated promptly, mitigating the risk of insider threats or data breaches.
- Separation of Duties (SoD): IGA systems can enforce SoD policies, preventing toxic combinations of permissions (e.g., the same person being able to create a vendor and approve a payment to them). This is crucial for preventing fraud and maintaining internal controls. SailPoint can identify and flag such violations, allowing organizations to remediate them before they become a problem.
The Role of AI in Modern IGA
Leveraging AI for Proactive Identity Management
What makes modern platforms like SailPoint’s Identity Security Cloud particularly strategic is the infusion of artificial intelligence. AI moves IGA from a reactive, rubber-stamping exercise to a proactive, intelligent process. How does this work in practice?
The AI engine analyzes massive datasets of access patterns across the organization. It identifies outlier permissions (for example, a user in accounting who has access to a software development tool that none of their peers do). It can then flag this as a high-risk permission during an access review, helping managers make more informed decisions. It can also recommend role definitions based on common access clusters, simplifying the creation of a clean, role-based access control (RBAC) model. This predictive capability helps organizations move from a reactive security posture to a more proactive one, anticipating and mitigating risks before they materialize.
Building Zero Trust Foundations
Ultimately, a strong IGA program is the foundation of a Zero Trust security posture. It operationalizes the principle of least privilege, ensuring identities only have the access they absolutely need to perform their job functions, and nothing more. It’s not the most glamorous part of cybersecurity, but it’s one of the most fundamental, providing the necessary visibility and control over who can access what within the enterprise.
I welcome your thoughts on the challenges of identity governance. Please connect with me on LinkedIn.